Blockchain Privacy Returns: From Ideals to Infrastructure
For most of crypto’s history, privacy lived in an uncomfortable middle ground: essential in theory, marginal in practice. Early narratives treated decentralization and financial privacy as inseparable, yet day-to-day behavior rewarded transparency. Public ledgers were convenient, auditable, and friendlier to regulators and institutions. Pseudonymity was widely treated as “good enough,” even as it steadily degraded under blockchain analytics, KYC chokepoints, and the growing ability to map on-chain activity to real-world identities.
That equilibrium began to change in 2025. Not because privacy suddenly became fashionable again, but because transparent finance started colliding with practical reality: individuals do not want every transaction, balance change, salary payment, or donation immortalized as a public record; businesses do not want to expose suppliers, payroll, counterparties, and treasury strategy to competitors; and institutions cannot move meaningful size on-chain if their positions and flows become instantly legible to the market.
One of the clearest behavioral signals came from Zcash. The network’s shielded supply climbed to nearly 25% of circulating ZEC, indicating that privacy usage is no longer a niche preference reserved for power users. More importantly, it suggests privacy is being reinterpreted: not as ideological purity, but as operational necessity.

Why Did Privacy Drift to the Margins in the First Place?
Crypto’s original trade-off was visible from the start. Bitcoin introduced a system that could be verified by anyone, at any time, without a central administrator. That verification came with a cost: radical transparency. Every transaction sits on a globally replicated ledger, and every link in the transaction graph can be studied indefinitely.
For years, that transparency was a feature rather than a bug. It made auditing straightforward. It enabled compliance teams to build monitoring systems. It allowed exchanges and custodians to offer simpler risk controls. Even for retail users, pseudonymous addresses felt private enough—until they were not.
Two developments changed the practical meaning of “good enough.” First, blockchain analytics matured into an industry. Second, the regulated perimeter tightened: centralized exchanges, stablecoin issuers, payment processors, and fiat ramps became high-signal identity layers. Once an address is linked to a verified identity, the privacy of prior and future activity often collapses, especially when users reuse addresses, interact with high-visibility protocols, or maintain a stable on-chain footprint.
Investor Takeaway
On-chain transparency helped crypto scale into regulated finance, but it also created a permanent “open balance sheet” problem for individuals and businesses. The 2025 privacy revival is less ideological and more about making on-chain activity usable at scale.
What Does Zcash’s Shielded Supply Signal About User Behavior?
Zcash has offered strong privacy for years, using zero-knowledge proofs to enable transactions that do not reveal sender, recipient, or amount. What changed in 2025 was less about new cryptography and more about context. Users increasingly internalized a simple truth: transparent wallets can behave like public bank statements. Once a wallet becomes “known,” an observer can often infer income patterns, spending behavior, holdings, counterparties, and even business relationships.
Zcash’s relevance in this environment is tied to selective disclosure. Rather than framing privacy as absolute anonymity, Zcash supports models where users can transact privately while still proving information when required for audits, compliance, or legal processes. That capability matters in a world where privacy tools face political resistance, but legitimate users still need discretion.
A rising shielded supply is not merely a technical metric. It is a behavioral metric. It suggests a growing portion of users are choosing privacy by default when it is available and usable, even without a hype cycle pushing the narrative.
Investor Takeaway
A rising share of shielded ZEC indicates real usage, not just ideology. Behavioral adoption is often a stronger long-term signal than price-driven narratives, especially in infrastructure categories like privacy.
Why Is Privacy Becoming a Business Requirement, Not a Protest?
The strongest argument for “pragmatic privacy” is not philosophical. It is operational. Transparent systems break normal commerce. A company that pays contributors on-chain exposes payroll strategy. A market-maker that rebalances inventory reveals position management. A treasury that rotates stablecoin exposure broadcasts credit risk preferences. In traditional finance, that information is protected behind bank confidentiality, broker controls, and legal safeguards. In crypto, it often becomes public by default.
This is why privacy has begun to re-enter the conversation as infrastructure. As crypto expands into payroll, B2B payments, tokenized real-world assets, and on-chain capital markets, confidentiality becomes less optional. For many enterprise use cases, transparency is not a nice-to-have; it is a deal-breaker.
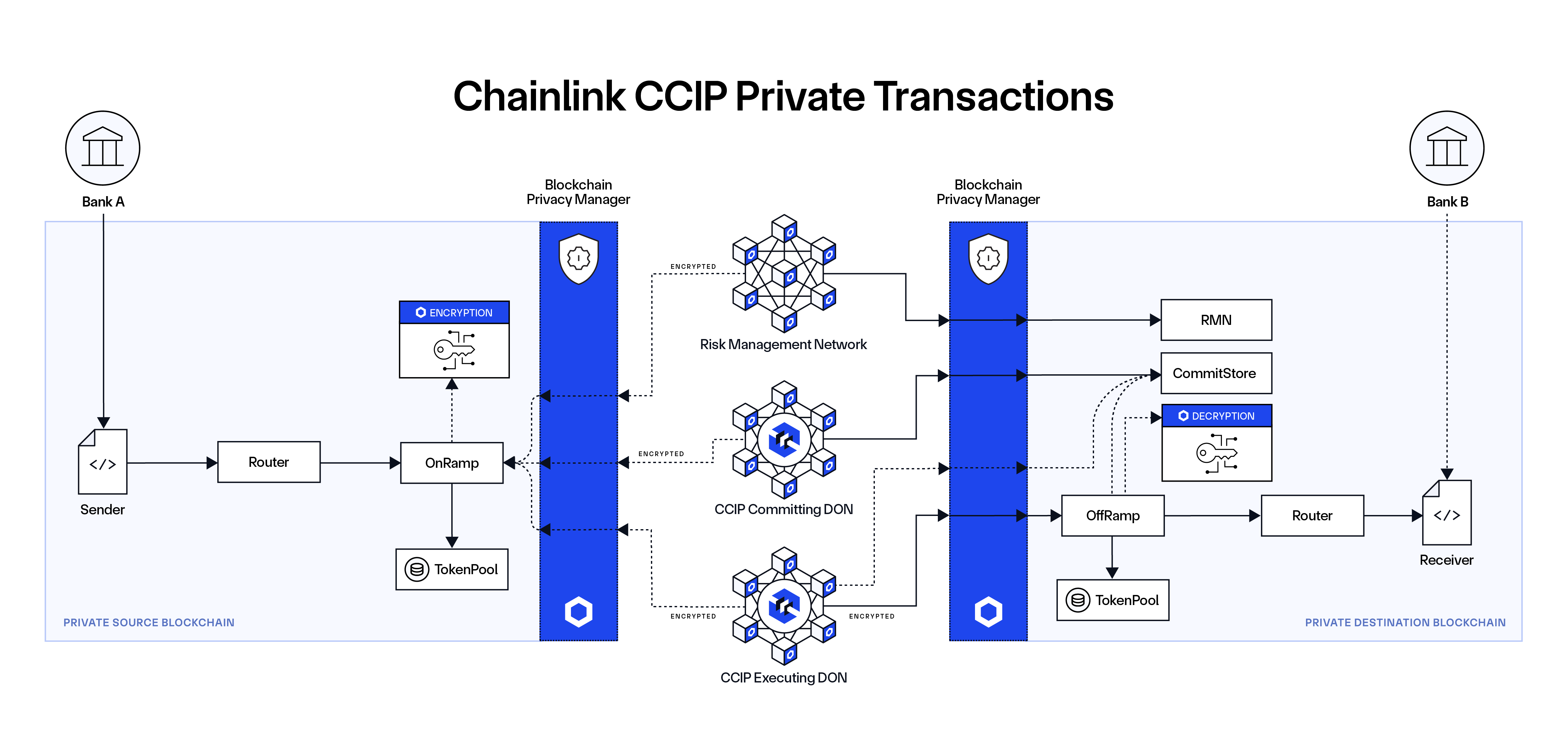
Investor Takeaway
Enterprise adoption pushes crypto toward confidentiality, not away from it. The winning privacy stack is likely to be the one that fits regulated workflows while still delivering meaningful discretion.
Which New Privacy Networks Are Emerging, and Why Now?
2025 saw privacy development expand beyond legacy “privacy coins” into a broader category: confidentiality layers built with modern zero-knowledge systems, modular integrations, and explicit compliance considerations. Instead of treating privacy as an add-on, new networks are attempting to bake it into protocol design.
Aztec Network’s Ignition Chain mainnet launch marked a major milestone for privacy on Ethereum’s scaling roadmap. Aztec’s core ambition is not simply to hide transaction details, but to enable private execution environments that still inherit Ethereum’s security assumptions. That distinction matters: privacy becomes more useful when it lives inside high-liquidity ecosystems, rather than as a separate island.

Nillion’s approach illustrates a parallel track. Instead of focusing only on private value transfer, it targets encrypted computation: the ability to process data without revealing inputs. That is a different privacy problem—closer to confidential computing and data security than classic transaction obfuscation—but it speaks to the same demand: businesses and applications want to use crypto rails without exposing sensitive information.
Other projects, including Cosmos-aligned initiatives emphasizing “composable privacy,” reflect an increasingly cross-chain reality. As capital moves across ecosystems, privacy risk compounds. A user may be private on one chain but exposed through bridging patterns, exchange deposits, or liquidity routing on another. Cross-chain activity increases the surface area for deanonymization unless privacy is designed as a system-wide feature.
Investor Takeaway
The privacy resurgence is shifting from “privacy assets” to “privacy infrastructure.” Investors should distinguish between speculative privacy narratives and protocols that can slot into major liquidity ecosystems with clear compliance pathways.
How Are Legacy Privacy Projects Adapting to the New Environment?
Legacy privacy projects are responding to a changed market structure. Liquidity, user experience, and regulatory survivability now matter as much as cryptographic strength. Projects that remain isolated risk becoming technically impressive but commercially irrelevant.
One strategic pattern is embedding privacy inside larger ecosystems. Rather than competing with high-liquidity chains, privacy projects are increasingly choosing to integrate as layers, rollups, or app-specific infrastructure. This approach reflects a hard-earned lesson: privacy is most valuable where economic activity is already concentrated.
Another pattern is selective disclosure and compliance tooling. The post-2022 era made it clear that privacy tools will be judged not only on what they can hide, but on how they can prevent abuse, support audits, and align with sanctions enforcement regimes. Protocols that can prove “clean funds” without revealing counterparties are trying to meet regulators halfway through cryptography rather than promises.
Investor Takeaway
Privacy protocols are being pushed toward integration and compliance-friendly primitives. Survivability may depend as much on “verifiable innocence” tools as on the strength of encryption itself.
What Are Coinbase, Circle, and Enterprises Actually Testing?
The clearest sign that privacy is becoming infrastructure is that corporations are experimenting with it openly. The motivation is straightforward: transparent ledgers are incompatible with many ordinary financial workflows.
Stablecoins are a prime example. If a company pays suppliers or employees in stablecoins on a transparent chain, counterparties and competitors can track flows in near real time. That can reveal margins, vendor concentration, and operational rhythm. Configurable privacy—where details can be hidden but selectively disclosed—offers a route to scale stablecoin usage beyond trading and into real commerce.
Enterprise networks reinforce the same theme. Confidential settlement layers, permissioned environments with cryptographic privacy, and tokenized asset rails all converge on one requirement: discretion is not a luxury feature for businesses; it is a baseline expectation.

Investor Takeaway
Corporate pilots suggest privacy is migrating from “niche crypto” to “enterprise requirement.” The most durable value may accrue to privacy rails that support stablecoins, payroll, and institutional settlement without violating compliance expectations.
Why Is Ethereum Treating Privacy as a Strategic Priority Now?
Ethereum’s posture toward privacy has shifted from optional tooling to strategic prerequisite. The logic is difficult to avoid: Ethereum can scale throughput via rollups and modular design, but it cannot become a core financial layer for institutions if every transaction is a public broadcast.
End-to-end privacy requires progress across multiple layers: wallets need user-friendly privacy defaults; applications need confidentiality primitives that do not destroy composability; and the protocol layer needs support for efficient proof systems and encrypted state transitions where appropriate. Treating privacy as a coordinated roadmap rather than isolated research is a signal that Ethereum sees confidentiality as part of its competitive moat.
This strategy also acknowledges political constraints. The market is searching for “default but compliant” privacy: privacy that protects ordinary users and businesses, while still allowing lawful disclosure when required. That framing is not pure cypherpunk. It is pragmatic infrastructure design.
Investor Takeaway
If Ethereum is serious about institutional scale, privacy cannot remain optional. A credible “default but compliant” path could unlock new on-chain flows that are currently blocked by transparency risk.
Can “Pragmatic Privacy” Survive Regulation and Sanctions Pressure?
The regulatory issue is not going away. Privacy tools have repeatedly collided with sanctions enforcement, anti-money-laundering obligations, and political narratives about illicit finance. This creates a structural challenge for privacy innovation: the stronger the privacy, the higher the perceived enforcement risk.
That tension is driving a category shift toward selective, verifiable privacy models. Instead of making everything opaque, newer approaches attempt to separate legitimate confidentiality from illicit concealment. Mechanisms such as association lists, proof-based screening, and cryptographic attestations aim to preserve privacy for compliant users while excluding flagged funds from protections.
These designs are not guaranteed to satisfy regulators. But they represent a meaningful evolution: privacy protocols are trying to encode compliance constraints into cryptographic systems, reducing reliance on trust or centralized gatekeepers.
Investor Takeaway
Regulatory survivability is the key risk for privacy infrastructure. Projects that can demonstrate privacy plus enforceable constraints may outperform purely opaque systems in regulated markets.
What Are the Market Risks and Failure Modes for Privacy Infrastructure?
Privacy may be rising in strategic importance, but it carries distinct risks. First, technical risk: zero-knowledge systems are complex, and implementation errors can be catastrophic. Second, usability risk: privacy that is difficult to use becomes an enthusiast feature rather than a mainstream default. Third, liquidity risk: privacy ecosystems that do not integrate into high-activity venues struggle to maintain relevance.
Fourth, and most importantly, policy risk. Privacy projects can face exchange delistings, infrastructure bans, or de facto exclusion from institutional rails depending on jurisdiction. Even if a protocol is technically compliant, the reputational burden of “privacy” can reduce distribution and partnerships.
Finally, there is a narrative risk: privacy can become a cyclical topic that spikes during surveillance controversies and fades during risk-on markets. The strongest projects will be those that solve continuous operational needs, not just ideological moments.
Investor Takeaway
Privacy is a high-utility category with high policy and implementation risk. Investors should evaluate privacy projects on integration, usability, and compliance posture, not cryptography alone.
How Should Investors Think About Privacy Exposure in 2026?
The most productive framing may be to stop treating privacy as a binary choice and instead treat it as a stack. At the asset layer, privacy-focused networks can benefit from renewed demand for confidentiality. At the infrastructure layer, privacy rollups, proof systems, and encrypted compute protocols may accrue value if they become embedded in major ecosystems. At the application layer, privacy-preserving payment tools, wallet defaults, and compliance-compatible mixers can become distribution channels for broader adoption.
Institutional adoption could be the catalyst that makes privacy durable. Institutions do not need total opacity, but they do need discretion. If crypto wants to compete with traditional financial rails in payments, settlement, and capital markets, it must offer confidentiality features that match baseline expectations from legacy systems.
Zcash’s rising shielded usage shows that, when privacy is available and usable, users choose it without needing a hype cycle. The broader ecosystem appears to be moving toward the same conclusion: privacy is not an ideological ornament. It is a prerequisite for normal economic life on-chain.
Investor Takeaway
The 2026 opportunity is not just “privacy coins,” but privacy as an embedded capability across major ecosystems. The strongest positioning may come from protocols that deliver confidentiality while remaining compatible with institutional compliance requirements.

Feature graphic suggestion (PNG, no text): a clean abstract visual showing layered privacy (wallet, app, protocol) as three translucent panels over a simplified blockchain grid, with a subtle “lock” icon motif and no labels.
[…] in 2026, Solana did not just top the ranking — it dwarfed every other network. BNB Chain, the second-place blockchain, processed less than one-fifth of Solana’s […]
[…] This framing arrives at a moment when stablecoins are no longer a niche crypto primitive. The USD-pegged stablecoin market is approaching $300 billion in circulating supply, dominated overwhelmingly by centralized issuers such as Tether and Circle. At the same time, decentralized alternatives remain marginal in scale despite being ideologically central to Ethereum’s long-term vision. […]
[…] firms inside the Dubai International Financial Centre to stop trading, promoting, or packaging privacy-focused assets like Monero and Zcash. No exchange listings. No funds. No structured products. No regulated […]